
In this attempt, attackers exploit DocuSign, a well-known electronic signature platform, to send convincing emails that prompt users to scan a QR code, leading them to a malicious Microsoft login page designed to harvest their credentials.
The attack begins with the victim receiving a legitimate-looking email from DocuSign, delivered from the official DocuSign domain. This email is carefully crafted to avoid suspicion and contains no malicious links or attachments, allowing it to bypass most email security filters.

Upon clicking the link within the email, the user is directed to the legitimate DocuSign portal, where they can view and interact with the document. However, within the document is a seemingly harmless QR code that the user is prompted to scan.
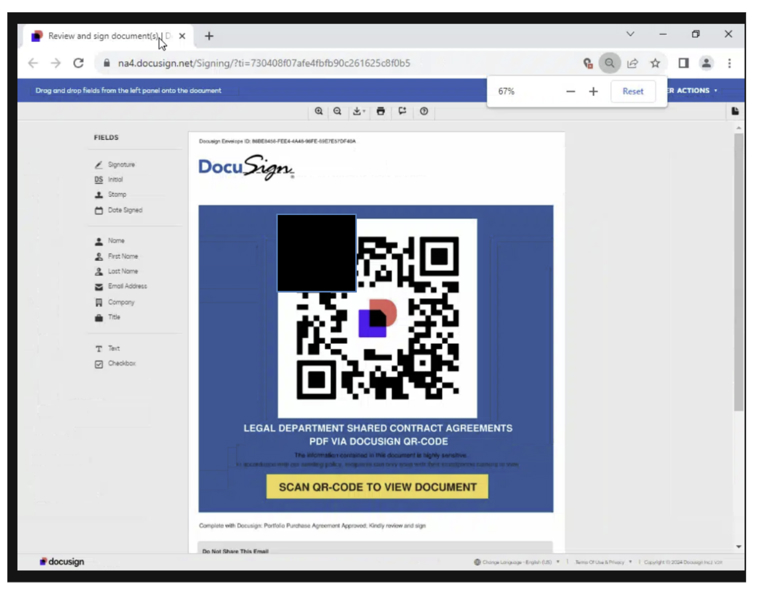
When the user scans the QR code, they are redirected to a malicious domain that mimics a Microsoft login page. This fake page is the crux of the attack, designed to trick the user into entering their Microsoft credentials. Once entered, these credentials are captured by the attackers for further exploitation.

• QR Code URL: https:// qrco. de/ bfTQau
This URL redirects users to the following credential harvesting page:
• Malicious Domain: https:// c1ient-index1oginauthonilne. aws-docusign-verify. workers.dev
This page is designed to resemble a Microsoft login page but is a credential harvester.
• Fake Microsoft Login Page: Hosted on a worker domain, this page captures the victim's credentials under the guise of a legitimate login prompt.
The phishing email originates from the official DocuSign domain, which gives it a high level of credibility, making it more likely to be trusted by recipients.
The email directs users to the legitimate DocuSign platform, further reducing suspicion. The attack vector leverages a QR code embedded in the document, which users are inclined to scan, particularly on mobile devices.
Ensure that employees are trained to recognize suspicious emails and the potential risks of scanning QR codes. As part of regular cybersecurity training, highlights the increasing use of QR codes in phishing campaigns.
Implement Multi-Factor Authentication (MFA) for all users. Even if credentials are compromised, MFA can prevent unauthorized account access.
Deploy mobile security solutions and Mobile Device Management (MDM) to monitor and secure mobile devices, reducing the risk of credential harvesting from devices that do not have sufficient security controls.
Encourage users to report any suspicious activity immediately to the security team. Early detection of phishing attacks can help prevent broader compromise.
If a similar incident or a BEC has occurred in the environment contact the Security Operations Centre.
By utilizing trusted platforms such as DocuSign and leveraging QR codes, attackers are able to bypass traditional security mechanisms. Organizations must remain vigilant, continue to educate users, and implement comprehensive security measures to mitigate the risks associated with such attacks.